CTF Write-up: Micro-CMS v1 (Hacker101)
Hacker101 CTF | Beginner Challenge | Full Flag Walkthrough
Hello everyone. I am Rudra, a software developer and cybersecurity enthusiast. This article is the beginning of a series of cybersecurity posts where I will be sharing my knowledge of hacking through CTF (Capture the Flag) walkthroughs. A CTF is a game designed to let you learn to hack in a safe, rewarding environment.
My first CTF involves the Micro-CMS v1 challenge from the Hacker101 CTF platform. It is a beginner-friendly challenge with multiple vulnerabilities.
🚩 Flag 0: Stored XSS
Opening Micro-CMS v1, I get access to three pages. I navigate to the "Create a new page" section. While editing the page title, I test for XSS with this payload:
Upon returning to the home page, the JavaScript executes — confirming a stored XSS. First flag captured!
🚩 Flag 1: SQL Injection
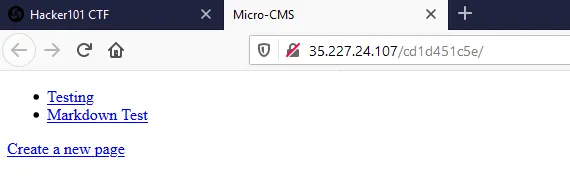
When editing a page, the page ID appears in the URL. I append a single quote ' to the end of the ID and observe the server’s response — revealing the second flag.
🚩 Flag 2: Unauthorized Access
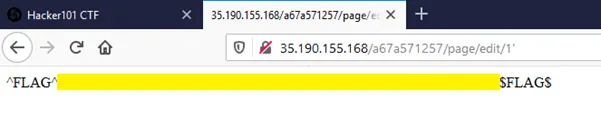
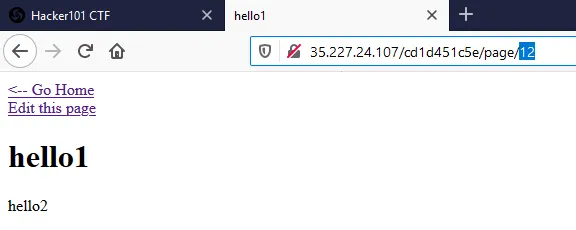
After creating a page, I see it's assigned an ID of 12. I probe other page IDs (e.g., 1 to 12). Page 7 returns a 403 Forbidden, not a 404. That means it exists and might be accessible differently.
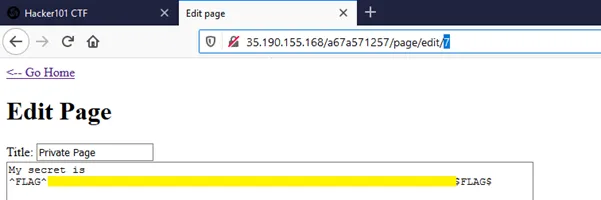
I attempt to edit the page with ID 7 directly and — success! The third flag is revealed.
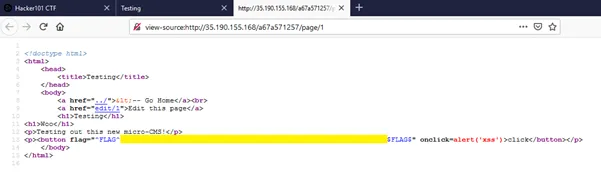
🚩 Flag 3: Stored XSS via Markdown
The body field supports Markdown, not script tags. I try various payloads and discover this one bypasses the filter:
🎥 Video Walkthrough
🐍 Python Script to Automate Flag Collection
from requests import get as get_request, post as post_request
from re import search as search_flag
ctf_url = f"https://" + input("\033[32m[1] Enter your ctf id: \033[0m") + ".ctf.hacker101.com"
FLAGS = []
try:
if get_request(ctf_url).status_code == 200:
print("\033[33m[2] Please wait while we fetch all flags.\033[0m")
# Flag via XSS
FLAGS += [f"^FLAG^{match.group(1)}$FLAG$"] if (match := search_flag(r"\^FLAG\^(.*?)\$FLAG\$", post_request(...).text)) else []
...
except Exception as e:
print(f"\033[31m[3] {str(e)}\033[0m")
print(f"\033[32m[3] Your flags are: {FLAGS}\033[0m")
📌 Takeaways
- Always test input fields for XSS — especially when they reflect data.
- Look for IDs in URLs and test for SQLi and access control issues.
- Try to break Markdown rendering to sneak in executable scripts.
- CTFs like this are great for learning web vulnerabilities hands-on.
🏷️ Tags
#Hacker101 #MicroCMS #CTFWriteup #EthicalHacking #WebSecurity #StoredXSS #SQLi #CTFChallenge #Skillshetra