Razorpay Payment Exploit PoC
Payment Hack on @giftlaya | Bug Bounty | Skillshetra
🚨 Critical Client-Side Payment Manipulation Vulnerability
During a security assessment of a Razorpay-integrated e-commerce platform, we discovered a critical vulnerability allowing attackers to manipulate the payment amount on the client side and complete orders by paying a fraction of the original price.
This attack works by intercepting the client-side payment request and modifying the amount field using tools like Burp Suite or Fiddler. Since the backend fails to verify the actual amount received from Razorpay, the order is marked as paid, even when only ₹2 is paid instead of ₹22,039.
🧪 Exploit Walkthrough (Step-by-Step)
- Go to the checkout page of the targeted Razorpay-integrated store (e.g., giftlaya.com).
- Initiate a legitimate purchase for a high-value item (e.g., worth ₹22,039).
- Open an intercepting proxy like Burp Suite and monitor the request made to Razorpay’s API.
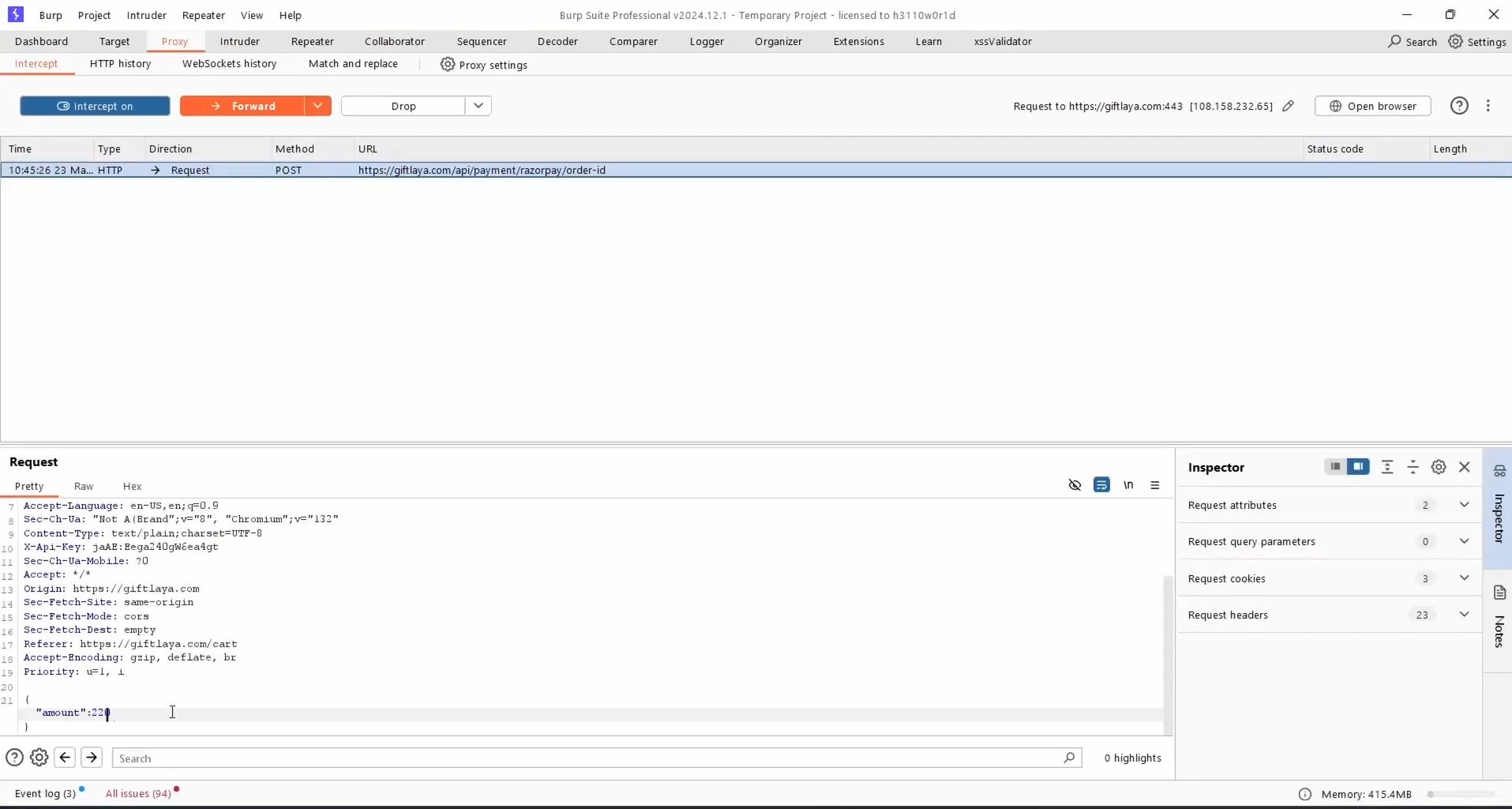
- Locate the field in the request body that contains the
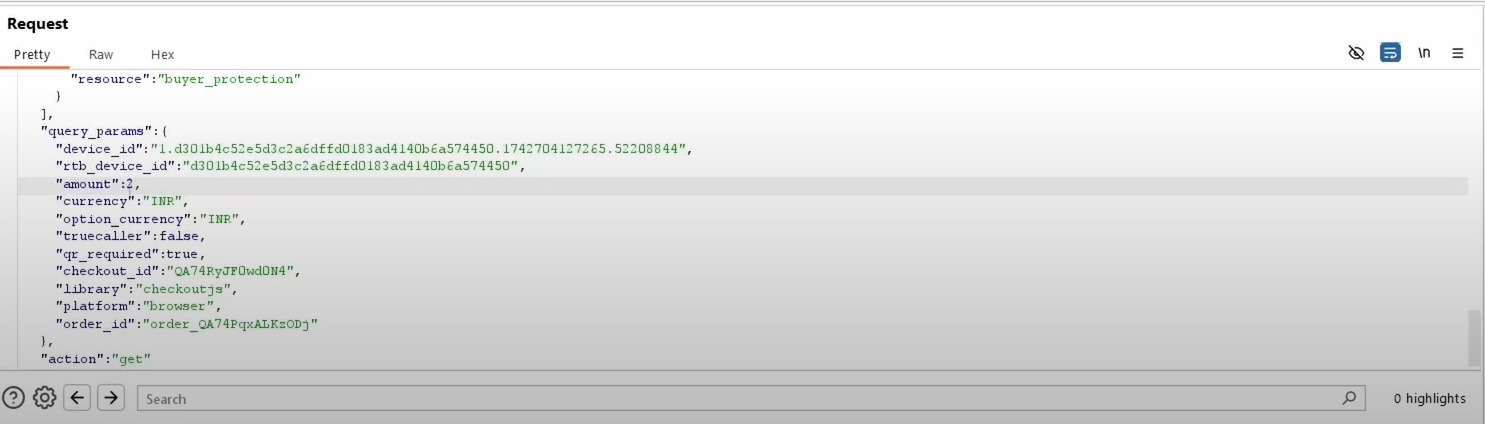
amountvalue. - Modify the amount from 2203900 (paise) to 200 (i.e., ₹2).
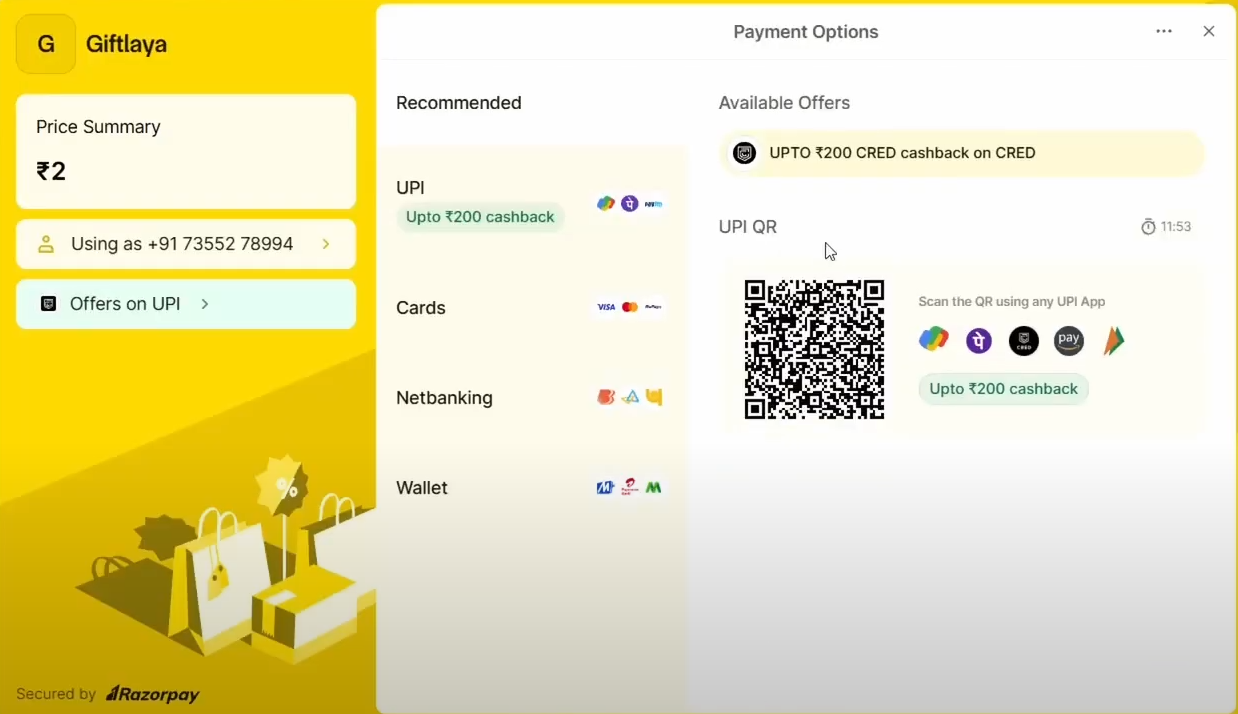
- Forward the modified request and complete the transaction with ₹2 via Razorpay.
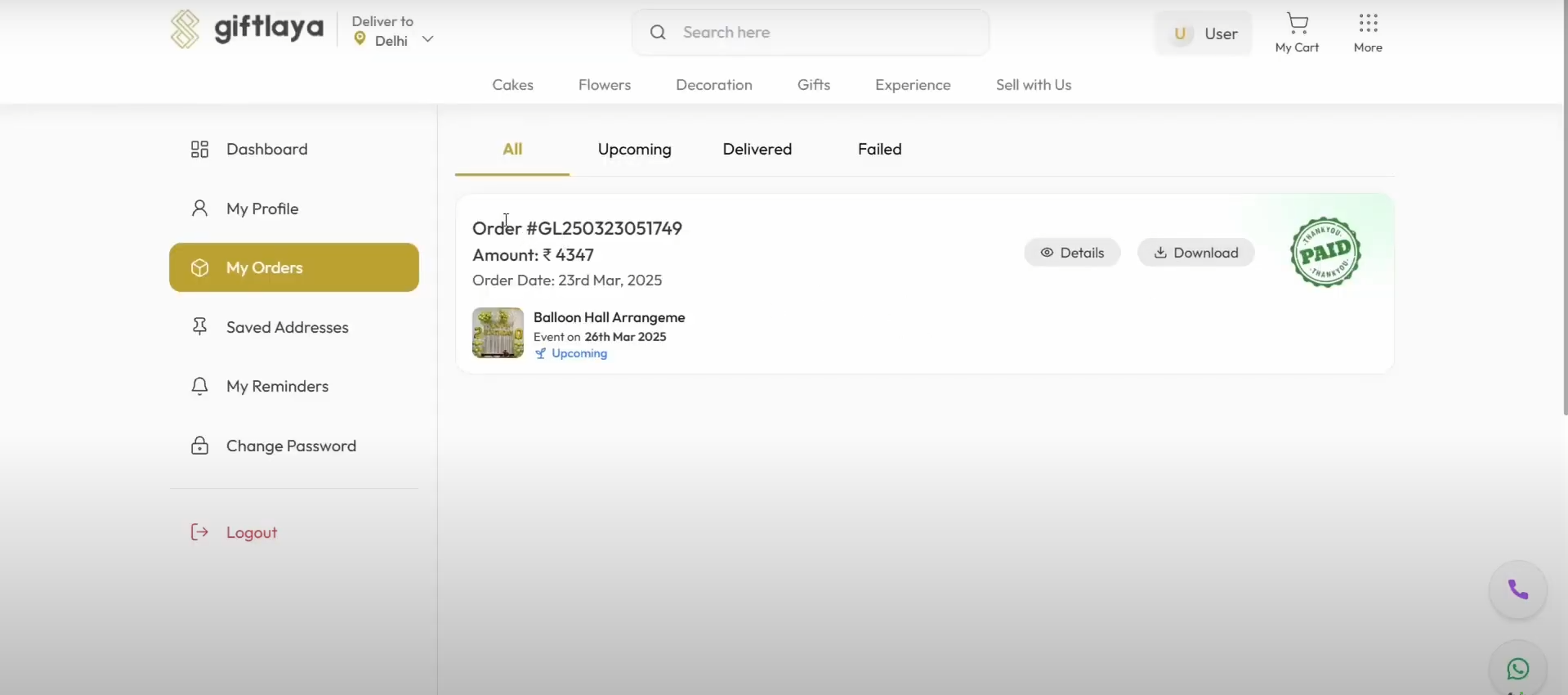
- Wait for the Razorpay success webhook to trigger — the system now incorrectly marks the expensive order as "Paid".
📸 Proof of Exploit (Screenshots)
1. Changing Amount in Checkout Request:
2. Modified API Payload:
3. Requesting Razorpay to Pay ₹2:
4. Order Confirmed for ₹22,039 by Paying ₹2:
📽️ Live Video Demonstration
🧠 Why This Is Dangerous
- Causes massive financial losses for merchants due to unpaid high-value orders.
- Exploits a lack of server-side verification of the transaction amount.
- Easy to replicate using basic intercepting proxies.
- Could lead to account takeovers, abuse of refund systems, and fraud scaling.
🛡️ How to Fix It
- Always verify the
amountreceived in Razorpay's webhook against the expected amount stored in your database. - Use Razorpay's `order_id` and `signature` verification properly on the server.
- Do not rely on client-provided prices or amounts — these can be manipulated.
- Implement integrity checks for cart contents and pricing before confirming payment.
📣 Tags
#CyberSecurity #BugBounty #Razorpay #EthicalHacking #Skillshetra #WebSecurity #PaymentGateway #HackingDemo #BurpSuite #ClientSideSecurity #OWASP