CTF Write-up: PostBook (Hacker101)
Recently I've started diving into CTFs and trying my hand at some Bug Bounties. This means that I will need to be writing reports with any bug I find and want to practice. So, here I go.
CTF Name: PostBook
Resource: Hacker101 CTF
Difficulty: Easy
Number of Flags: 7
Note: NO, I won't be posting my found FLAGS, but I will be posting the methods I used.
🏁 Flag 0
Goal: The person with username "user" has a very easy password...
Acquired By: username: user and password: password.
Thoughts: This is an easy one. Tried user as password first, failed. Then tried password and boom, flag!
🔍 Flag 1
Goal: Try viewing your own post and then see if you can change the ID
Acquired By: Changing the id=# in this URL: index.php?page=profile.php&id=d
Thoughts: Classic IDOR. URL manipulation is risky if not validated properly. Should always sanitize and restrict input!
🕵️ Flag 2
Goal: Use "Inspect Element" on the form when creating a new post
Acquired By: Changed a hidden field (user_id) to post as another user.
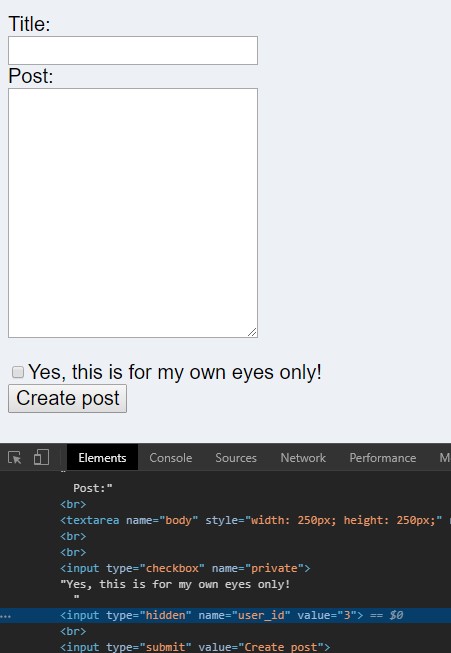
Thoughts: Hidden fields aren't secure. Always validate data server-side.
🧮 Flag 3
Goal: 189 * 5
Acquired By: Calculated ID = 945 and accessed the post with that ID.
Thoughts: Predictable numeric IDs are a red flag. Use UUIDs or protect endpoints.
✏️ Flag 4
Goal: You can edit your own posts, what about someone else's?
Acquired By: Manipulated the post ID in the edit button's HTML.
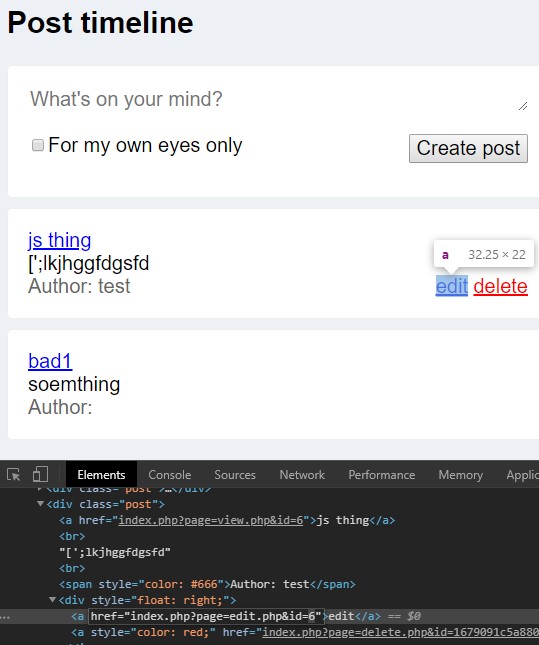
🍪 Flag 5
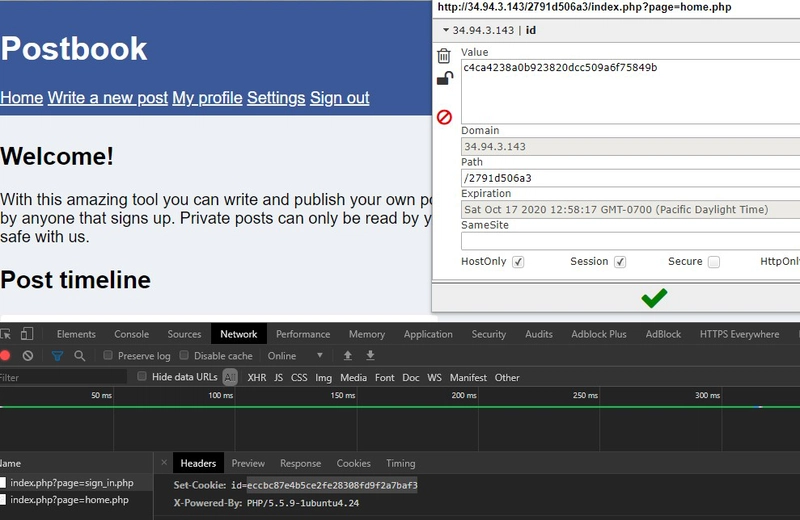
Goal: The cookie keeps you signed in. Can you log in as user ID 1?
Acquired By: Inspected the cookie (MD5 hash of user ID). Replaced with MD5 of 1, and it logged me in as user 1.
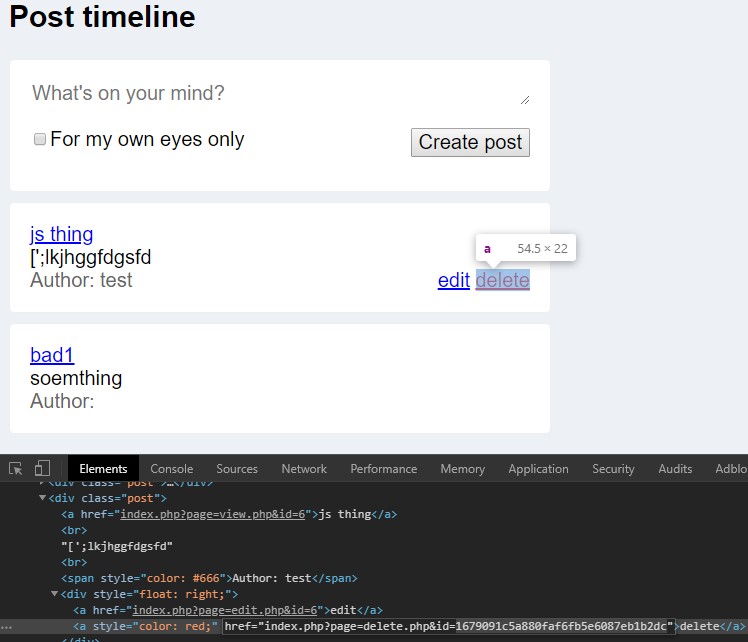
🗑️ Flag 6
Goal: Deleting a post takes an ID that’s not a number?
Acquired By: Used MD5 hash in the ID for the delete request. Got the flag by replacing the hash with another user’s ID in hash form.
📚 What I Learned
I learned a lot about manipulating cookies and maneuvering between user accounts here. While this was an easy-level challenge, real-world sites still suffer from these vulnerabilities. New developers need more training in secure coding practices.
Happy Hacking! 🧠💻